Cyber security is a growing concern in all parts of the world, with the roll out of 5G networks in many countries, building effective 5G cyber security strategies will be key for protecting networks and end-user data.
Key 5G cyber security challenges include multiple domains, multi-services, and multi-access which present threats such as security complexity to deal with multiple levels across domains, more dynamic and multifaced attacks, plus the perimeter security model becoming insufficient respectively.
In 2020, Huawei passed the 5G Core (5GC) Network equipment Security Assurance Scheme (NESAS) and Security Assurance Specifications (SCAS) assessment becoming the first company to complete GSMA’s NESAS evaluation.
NESAS includes security assessments of vendor development, product lifecycle processes, and Security Assurance Specifications, it acts as a mobile industry-wide network security evaluation framework that is efficient and open to evolution.
Objectively NESAS measures how secure a network product is and Huawei having passed the assessment, is supporting GSMA and 3GPP on developing globally standardized security evaluations. By this standard, key 5G cyber security strategies must include the following standards.
A Layered 5G Cyber Security Model Renowned in the Industry
The 3-layer security model is widely accepted in the telecommunications industry including institutions like 3GPP, 5G PPP, among others.
On Layer 1 product security through standard compliance, SDL security development life cycle and NE protection are realized with operation devices including base stations, routers, and the network core.
Layer 2 network security involves secure deployment of network equipment, connection to the 5G Core, O&M security, and network protection. To the top, layer 3 involves application security, sp compliance, and service protection to terminal and vertical application providers including device apps.
As listed through the layered security model, 5G security requires “shared responsibility” among different stakeholders at all levels of operation.
4. Top-level Design Principles for 5G Cyber Security
When Level 2 Network security is combined with level 1 product security, basic principles on 5G cyber security can be achieved. Principal 1 involves in-depth defense, and includes protection against border intrusion and lateral movement attacks with Anti-Dos, access control, encryption, and anti-tampering as key mechanisms.
Principle 2 Zero trust @ 5G involves continuous evaluation and dynamic authorization with anti-spoofing, and anti-elevation of privilege as execution mechanisms.
Principal 3 on adaptive security involves dynamic, continuous optimization based on Identify, Protect, Detect, Respond, and Recover (IPDRR) with continuous detection and proactive closed-loop control as key mechanisms.
7. Adaptive Security: Continuous Detection and Proactive Closed-Loop Based on the IPDRR Methodology
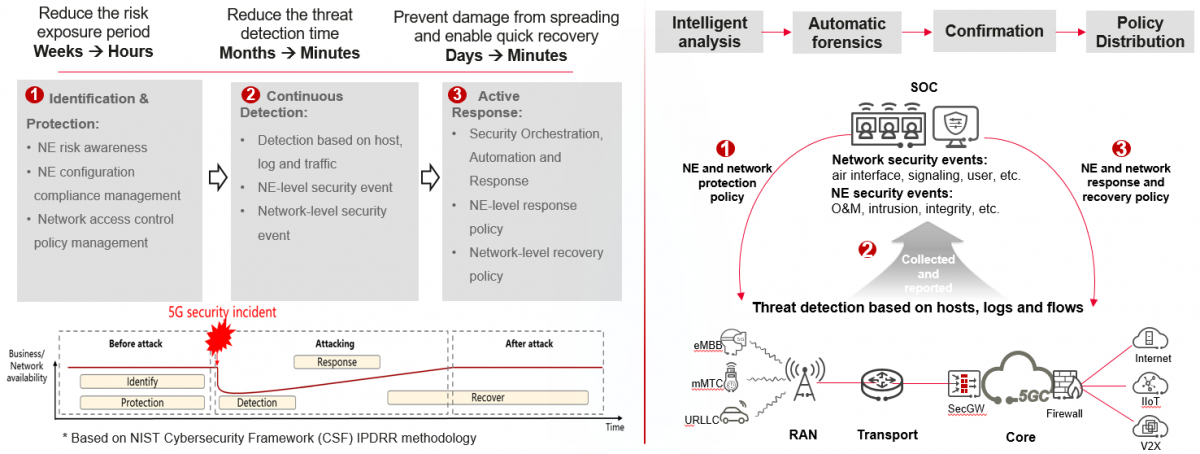
Intelligent analysis, automatic forensics, confirmation, and policy distribution contribute to the integration of adaptive security through building intrinsic 5G security capabilities and developing dynamic security solutions that are continuously optimized in form of a cycle.
Conclusion
To build effective 5G cyber security strategies, it’s important to note that 5G cyber security is a shared responsibility of key stakeholders such as Mobile Network Operators (MNOs), vendors, application providers, and regulators.
Report is from Huawei Uganda 5G Expert Mr. Franklin.





